- E2EE Implementations and Configurations
- Secure Messaging Platforms and User Authentication
- Key Management, Device Security, and Employee Training
- Requires E2EE Protection that Identify and Classify Sensitive Data
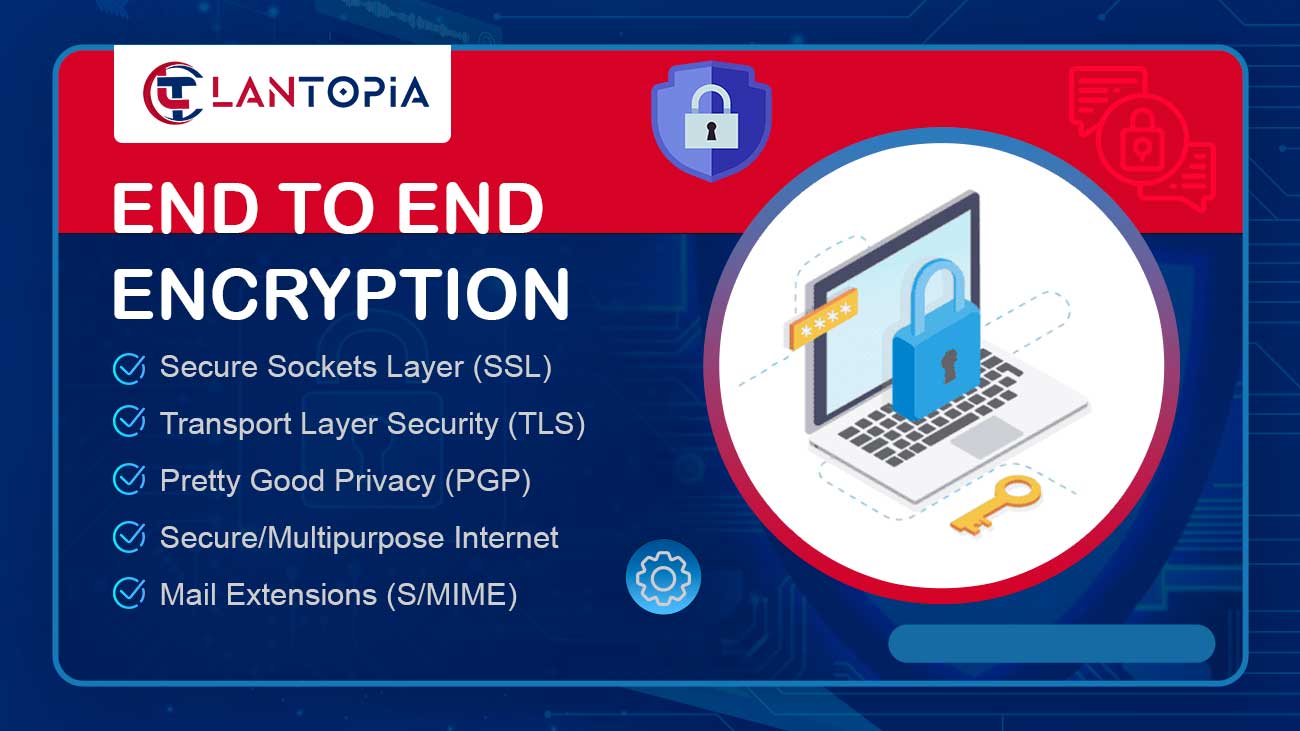
LANtopia provide encrypted email website and encrypted email services
If you want to create an encrypted email website or you need encrypted email services , we provide PGP encryption RSA 4096-bit encryption key AES 256-bit encryption SSL/TLS encryption SSL/TLS certified SSL certified end-to-end encryption zero to protect your data.
can give you access to data, and your recipient can read your emails. Messages cannot be read by anyone else, your IP address is removed from logs and metadata. No IP logs, no metadata logging, nothing stored or retrieved or read by third parties. (All outgoing emails are anonymous to you. Your IP will not be known, and this email server will use the IP for all emails. Additionally, mailboxes are not linked to IP addresses in any way. .) Zero knowledge passwords will be protected. Using zero-knowledge password protection technology, so that no one knows your private key password, and no one will be able to access your encrypted data through any means.
What can you expect to pay? We believe in being up-front with our prices as we respect our customers.
- Remote services are billed at $50/hr
- On-site services are $100/hr with a travel fee of $100 per visit
- A monthly retainer starts from $500 which accounts for 15 remote hours of support. This adds 50% bonus support hours for free and is the most economical and preferred by our customers.
What can you expect to get?
Dedicated IT professional with deep knowledge of the technologies needed to help your business. Recommendations on best practices. Fast turnaround and highest quality work with a proven track record.
We guarantee satisfaction or your money back.
- Definition and Understanding
- Clearly define what end-to-end encryption (E2EE) means for your business
- Ensure a comprehensive understanding of E2EE among employees and stakeholders
- Data Classification
- Identify and classify sensitive data that requires E2EE protection
- Clearly define what types of information should be encrypted end-to-end
- Communication Channels
- Implement E2EE for communication channels such as messaging, email, and collaboration tools
- Choose tools and platforms that support E2EE or consider implementing additional encryption layers
- File and Data Storage
- Encrypt sensitive files and data at rest using E2EE
- Choose storage solutions that support E2EE or implement additional encryption mechanisms
- Secure Messaging Platforms
- Use secure messaging platforms that offer end-to-end encryption
- Verify the security features of communication tools used within the business
- User Authentication
- Implement strong user authentication measures
- Ensure that only authorized users have access to the encrypted data
- Key Management
- Establish a robust key management system for encryption keys
- Implement secure practices for key generation, distribution, and storage
- Device Security
- Ensure the security of devices used to access encrypted data
- Implement device management policies to secure endpoints
- Employee Training
- Provide comprehensive training on the importance of E2EE
- Educate employees on best practices for securely handling encrypted data
- Integration with Security Policies: Align E2EE implementation with overall cybersecurity policies. Ensure that E2EE practices are integrated into broader security protocols.
- Compliance and Regulations: Ensure compliance with industry-specific regulations regarding data encryption. Stay informed about changes in data protection and privacy laws.
- Collaboration Tools: Select collaboration tools that offer E2EE for shared documents and communications. Confirm that collaborative features do not compromise end-to-end encryption.
- Mobile Device Security: Implement E2EE for data transmitted between mobile devices. Enforce security policies for mobile devices accessing encrypted data.
- Secure Backup and Recovery: Implement secure backup solutions that maintain E2EE. Establish recovery procedures that preserve encryption during data restoration.
- Vendor and Third-Party Security: Ensure that third-party services and vendors handling encrypted data follow E2EE practices. Verify the security measures of cloud providers or external partners.